$1.46 billion stolen in a single crypto heist.
Let that number sink in.
Last Saturday morning, post-run coffee in hand, I opened up the news expecting the usual cybersecurity headlines, only to be hit with this record-breaker: North Korea's Lazarus Group had just pulled off their most audacious attack yet on Bybit.
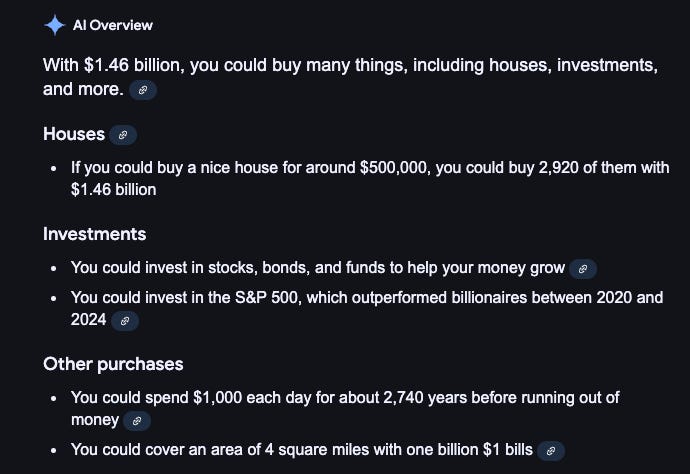
If you’re wondering (like I was) what you can buy with $1.46 billion - here’s a quick summary from Google:
Point being: this is a lot of money. The most ever in a single crypto heist.
This isn't just another heist, it's a stark warning of how cybercriminals, particularly state-sponsored actors, are continuously pushing the boundaries of what's possible. According to Chainalysis, North Korea stole $1.34 billion across 47 cryptocurrency hacks in 2024 alone, accounting for 61% of all ill-gotten crypto.
While some reports suggested the DPRK was slowing down their activity in the latter half of 2024, this weekend's unprecedented Bybit attack proves quite the opposite. Based on recent trends, even this record-breaking heist won't hold its place in the history books for long.
Ok, So What Happened?
The Bybit heist is yet another sophisticated operation orchestrated by North Korea’s Lazarus Group, leveraging a multi-pronged attack strategy that combines credential theft, social engineering, and smart contract vulnerabilities.
The attackers gained unauthorized access by exploiting weaknesses in Bybit’s internal security controls, possibly through compromised employee credentials obtained via spear-phishing or supply chain attacks.
Once inside, they navigated through layers of security, leveraging lateral movement techniques to escalate privileges and extract private keys. The final stage of the attack likely involved automated scripts executing rapid asset transfers, bypassing detection thresholds by distributing funds across multiple wallets before laundering them through decentralized exchanges and privacy-focused cryptocurrencies like Monero.
The precision and speed of the heist suggest extensive pre-attack reconnaissance, deep knowledge of Bybit’s internal security posture, and the use of advanced obfuscation techniques. The Lazarus Group once again demonstrated its ability to operate at an elite level, disappearing with $1.46 billion before Bybit could respond effectively.
Crypto Heists: A Growing Threat with a Long History
The Lazarus Group's track record reads like a greatest hits album of cyber crimes. Their expertise in targeting crypto exchanges and DeFi platforms has only grown more sophisticated with each attack. Infamous examples include:
Ronin Network Hack (2022): A staggering $620 million stolen in one of the largest DeFi heists in history, targeting the blockchain network supporting the Axie Infinity game.
CoinCheck Hack (2018): $530 million vanished in a sophisticated breach targeting Japan-based crypto wallets.
Bangladesh Bank Heist (2016): While not crypto-related, this attack on SWIFT banking transactions demonstrated their evolving capabilities, resulting in $81 million stolen from a planned $850 million heist.
These attacks illuminate an unsettling reality: Attackers are continuously innovating to stay ahead of security measures. From private key theft to smart contract exploits, their playbook keeps expanding—with DLL sideloading remaining a surprisingly effective constant for persistence and cryptomining.
But while high-profile heists like Bybit’s grab headlines, not every cybercriminal is aiming for a billion-dollar payday overnight. Some attackers take a slower, more insidious approach—stealing from organizations not in a single transaction, but continuously, over months or even years. This brings us to cryptojacking, an increasingly prevalent and stealthy form of digital theft.
Cryptojacking: The Silent Revenue Stream That's Growing Louder
Cryptojacking, once heralded as the new ransomware, is not grabbing headlines the same way its infamous cousin is. Nevertheless, its insidious persistence has plagued security teams for almost a decade. During my time as a Global Solutions Architect at CrowdStrike, I authored a blog about the “rise” of a new threat vector: cryptojacking.
Six years later, it's evolved into something far more sophisticated—stealthier, more profitable, and more efficient than ever before.
Understanding Modern Cryptojacking
Today's cryptojacking operations follow the sophisticated patterns of advanced persistent threats. Attackers begin by infiltrating systems through phishing, software exploits, or supply chain attacks. In cloud environments, they target poorly secured accounts to mine Monero at unprecedented scale.
Container environments aren't safe either—attackers exploit Kubernetes and Docker deployments with increasing frequency. Through DLL sideloading, scheduled tasks, and process injection, these operations can persist undetected for months or even years.
The Real-World 2024 Cryptojacking Campaign: GhostEngine
A prime example is GhostEngine, a cryptojacking campaign discovered in 2024 that disabled endpoint detection and response (EDR) solutions before deploying mining malware. The attackers exploited vulnerable drivers to terminate security software, ensuring their Monero miner ran undetected. GhostEngine showed a new level of sophistication in cryptojacking operations by blending DLL sideloading, kernel-level exploits, and cloud hijacking to persist across environments.
Practical Detection Strategies for Security Teams
Whether you're working with enterprise security tools or building detection capabilities from scratch, here's your actionable roadmap for hunting cryptojacking activity. Not everyone is going to hear the fans spinning up in off-hours in AWS US-East 1.
Thankfully, we can query our SIEM to find sudden spikes in compute resources. Here are specific queries and approaches that work in real-world environments:
Unusual CPU/GPU Usage: Sudden spikes in compute resources, even on idle systems.
SIEM Query (Splunk):
index=cloud_metrics sourcetype=cpu_usage
| stats avg(cpu_usage) by instance_id
| where avg(cpu_usage) > 80
Outbound Connections to Cryptocurrency Mining Pools: Domains like xmrpool.eu, supportxmr.com, and minexmr.com.
SIEM Query (Elastic):
source.ip: * AND destination.domain: ("xmrpool.eu" OR "supportxmr.com" OR "nanopool.org")
Unauthorized Processes: Unexpected processes like xmrig, minerd, or cpu-miner.
YARA Rule:
rule Cryptojacking_Process
{
meta:
description = "Detects potential cryptojacking activity"
strings:
$coinminer = "xmrig" nocase
$pool = "stratum+tcp://" nocase
$wallet = "wallet.dat"
condition:
any of them
}
These are simple, but I hope they’re enough to get started. Understandably Splunk and Elastic aren’t necessarily “cheap” - yet these high level threat hunts should yield value if your organization is currently experiencing cryptojacking…and help with resource load balancing.
MITRE ATT&CK Mapping for Cryptojacking
If you’re a reader of this substack, you know I love my MITRE mappings. See below to understand and mitigate cryptojacking threats by mapping known techniques to MITRE ATT&CK:
As a visual aide, here’s a MITRE ATT&CK navigator visual to help demonstrate the kill-chain.
Screenshot: MITRE ATT&CK Navigator View (cropped)
Where to Start Today
Proactive Defense Measures
Let’s start with the basics: cyber hygiene. If you’re able to harden and observe your environment, it should provide a first, robust gate against cryptojacking activity.
Harden Cloud APIs: Restrict access to admin interfaces (Docker, Kubernetes) and use strong authentication.
Enable Process Monitoring: Alert on unauthorized execution of known miner binaries.
Monitor Network Traffic: Block outbound connections to known mining pools.
Apply Security Updates: Patch vulnerabilities used in cryptojacking exploits.
Use the hunts provided
This list is not exhaustive, but it’s a great starting point when it comes to readying yourselves against cryptojacking.
Now to operationalizing this list. Here’s a suggested strategy broken out in steps, prioritized by impact and ease of implementation:
Immediate Actions (Week 1):
Deploy process monitoring for known mining binaries
Block outbound connections to common mining pools
Review and harden cloud API access controls
Short-term Improvements (First Month):
Implement the provided SIEM queries
Deploy YARA rules across your environment
Establish baseline resource usage patterns
Ongoing Maintenance:
Regular review of detection rules
Update blocked mining pool lists
Monitor for new cryptojacking techniques
Final Thoughts: The Evolution of Crypto Threats
While North Korea's Bybit heist currently holds the record, the real threat landscape is more nuanced. Cryptojacking shows us that not every attack needs to be a dramatic heist to be devastating. It's a reminder that effective security isn't just about preventing the big heists, it's about maintaining visibility and control across your entire environment.
For security teams, the message is clear: start with the basics, build robust detection capabilities, and operationalize them. Whether you're defending against billion-dollar heists or protecting CPU cycles, the fundamentals of good security hygiene remain your strongest ally.
Stay curious, stay secure, and happy hunting.
Damien